תוכנות זדוניות של BIOPASS משתמשות בתוכנת הזרמת OBS Studio כדי להקליט מסכי קורבנות
טרנד מיקרו גילה BIOPASS malware that attacks and spies on users of Chinese gambling sites. The researchers speculate that the well-known spy hack group Winnti (APT41) may be behind the creation of this malware.
BIOPASS is a Remote Access Trojan (עכברוש) written in Python. בדרך כלל, it hides inside the legitimate installers of Adobe Flash Player or Microsoft Silverlight, which are still in use in China, even though they are no longer supported in the rest of the world.
Experts write that malicious JavaScript is used to spread the malware, which is hosted on technical support or chat pages of Chinese gambling sites. It redirects users to pages that offer infected installers to potential victims. If a user fell for this trick of cybercriminals, BIOPASS penetrated his system.
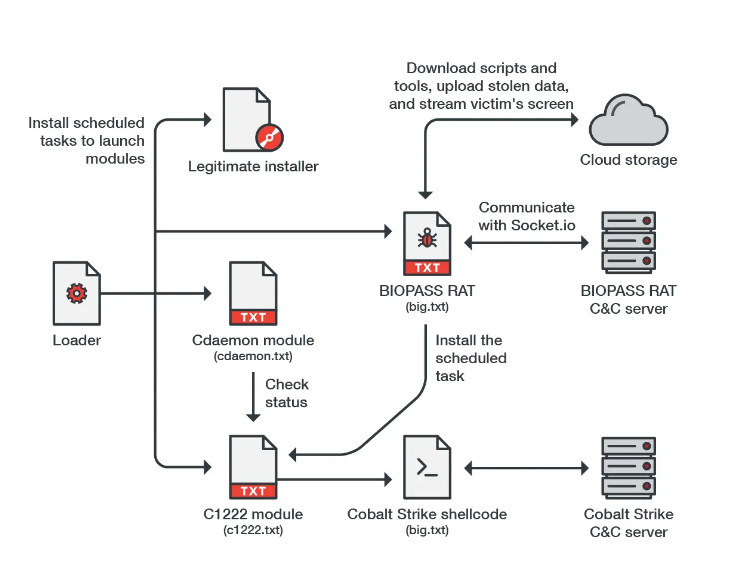
Malware differs little from other RATs and has such features as file system evaluation, remote desktop access, file stealing and shell-command execution. The malware can also compromise the personal information of victims by stealing data from browsers and instant messengers (including QQ Browser, 2345 Explorer, Sogou Explorer and 360 Safe Browser, WeChat, QQ and Aliwangwang).
An interesting feature of this malware is the use of the popular streamer software OBS Studio, which is often used by users of Twitch, YouTube, וכולי. The attackers used RTMP in OBS Studio to capture the user’s screen and broadcast video directly to the malware control panel.
מעניין, the Winnti group, which is allegedly responsible for creating the malware, is known as a Chinese cyber espionage group. Sometimes, with the aim of gaining personal gain, Winnti arranges attacks on gambling companies in Southeast Asia. Since in this case the attacks are targeting Chinese users, the researchers are not too sure about their attribution.
תן לי להזכיר לך שגם אני כתבתי את זה האקרים סינים מכסים את עקבותיהם ומסירים תוכנות זדוניות מספר ימים לפני הגילוי.




