연구원들은 Windows Server 컨테이너 및 Kubernetes 클러스터를 대상으로하는 Siloscape 맬웨어를 발견했습니다.
Researchers at Palo Alto Networks 발견했다 a highly obfuscated Siloscape malware that breaks into Windows Server containers in order to compromise Kubernetes clusters. The ultimate goal of attackers is to deploy a backdoor that can be used for other malicious activities.
Experts write that for the first time such attacks were noticed in early March, but they have been going on for at least a year. The attackers behind this campaign scan the network for common cloud applications and then use exploits against them for various old vulnerabilities.
If a web application is running inside a Windows Server container, attackers use the Siloscape malware, which exploits the previously documented escape container method to gain access to the underlying OS.
If the OS is running as a Kubernetes node, hackers also extract the node’s credentials and then use them to navigate to the Kubernetes back-end infrastructure and deploy new nodes with malicious features.
Siloscape also downloads and installs a Tor client on the infected system to communicate with its C&C server and receive commands from its operators via IRC.
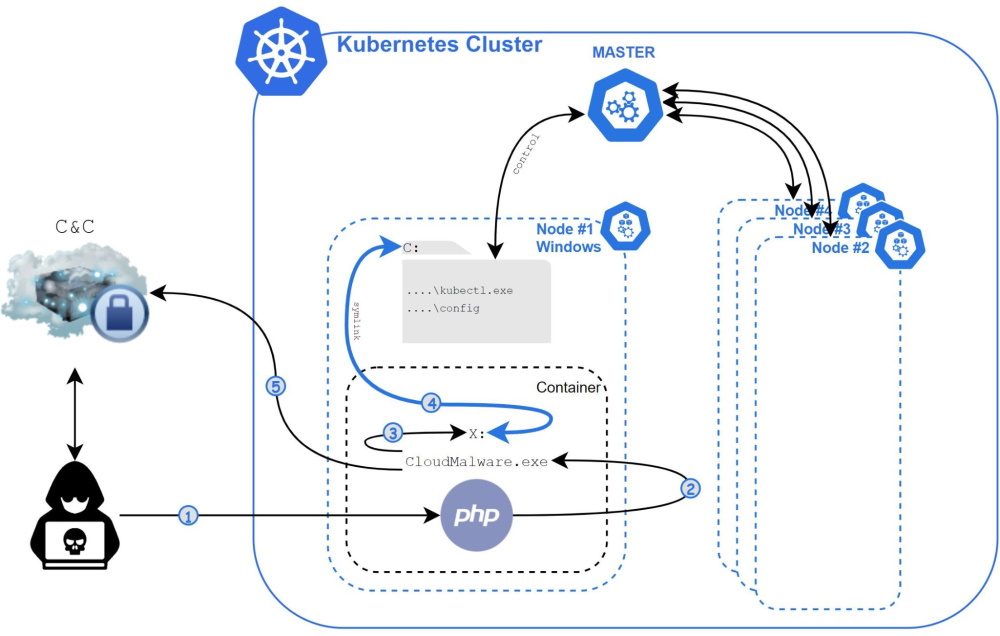
Palo Alto Networks company specialists report that they was able to gain access to this server, and currently attackers have infected more than 300 시스템. 동시에, the ultimate goal of the hackers is not completely clear.
“Unlike other malware targeting containers and mainly targeting cryptojacking, Siloscape doesn’t actually do anything to damage the cluster itself. 대신, it focuses on ensuring that it cannot be detected and tracked, and opens a backdoor into the cluster,"라고 전문가들은 말한다..
It is speculated that attackers could lease to other criminals access to some of the larger compromised companies, including the ransomware operators.
연구원에 따르면, companies should start moving applications from Windows containers to Microsoft Hyper-V as soon as possible, as Microsoft itself recommends using Microsoft Hyper-V instead of the old and less secure container mechanism.
Siloscape shows the importance of container security, as the malware wouldn’t be able to cause any significant damage if not for the container escape. It is critical that organizations keep a well-configured and secured cloud environment to protect against such threats.




