Το Coper Banking Trojan στοχεύει σε χρήστες της Κολομβίας
Doctor Web has discovered a new family of banking Trojans for Android named Android.BankBot.Coper (στο εξής Coper). While the bankers are targeting Colombian users, ωστόσο, the researchers believe that over time, versions may appear that will attack users from other countries.
It is reported that this family of malware has a modular architecture and a multi-stage infection mechanism, as well as a set of protective techniques to help resist deletion.
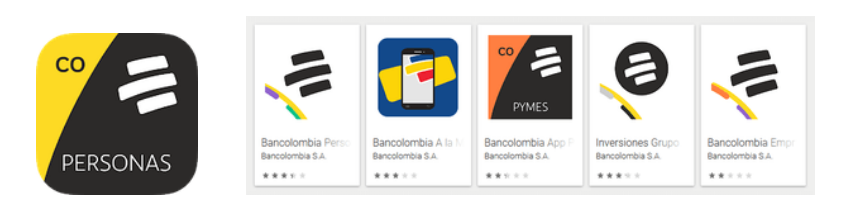
All Coper samples found were distributed under the mask of the official software of the credit institution Bancolombia (Bancolombia Personas applications). To make them more convincing, their icons were designed in the same style as those of the real programs of the bank.
For comparison, below is an example of a fake icon (left) and an example of real Bancolombia app icons (right) available for download on Google Play.
The infection process is divided into several stages. The first step is to install a decoy program that cybercriminals impersonate as a real banking application. στην πραγματικότητα, it is a dropper whose main task is to deliver and install the main malicious module hidden inside it on the target device.
During the installation process, the banker gains access to Accessibility Services, with the help of which it can fully control the infected device and imitate user actions (για παράδειγμα, clicking on menu buttons and closing windows). Για να το κάνω αυτό, he asks the victim for the appropriate permission, and having received it, it tries to disable the Google Play Protect protection built into the operating system, allow the installation of applications from unknown sources, install and run the main malicious module and also provide it with access to special features.
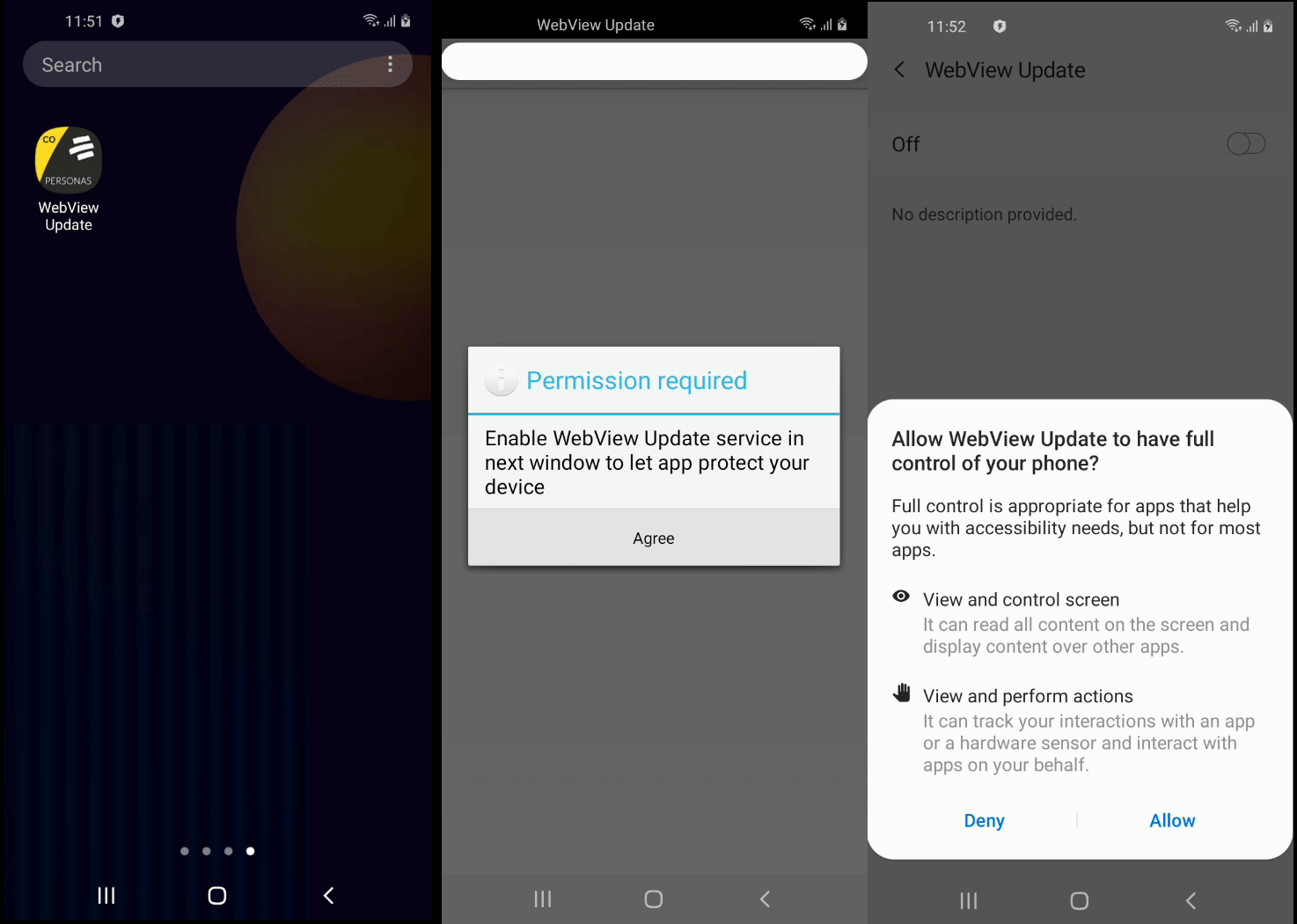

The main Trojan module that performs the main malicious actions is installed under the mask of a system application named Cache plugin, which uses the gear icon, which is standard for some Android system programs. The name and icon increase the likelihood that users will not see a threat in the program.
Όταν εκτοξεύτηκε, this module gains access to a number of important functions. Για παράδειγμα, the Trojan asks for permission to read and manage notifications and add them to the list of exceptions for system battery optimization, which will allow it to work permanently. Επιπλέον, the Trojan becomes the administrator of the device and also gains access to control phone calls and SMS messages.
Περαιτέρω, this module hides its icon from the list of applications on the main screen, concealing it from the user, after which it informs the C&C server about the successful infection of the device and waits for further instructions.
The banker maintains constant communication with the server, sending requests to it every minute. If necessary, this interval can be changed by the appropriate command.
Επιπλέον, depending on the response received from the server, the Trojan can change its other settings, συμπεριλαμβανομένου:
- a list of command-and-control servers;
- a list of target applications that will display phishing windows when launched;
- a list of programs to be removed;
- a list of applications that the Trojan will prevent from launching by returning the user to the home screen;
- a list of programs from which notifications will be blocked;
- other parameters.
Having received the right command from its operators, Coper is able to:
- execute USSD requests;
- send SMS;
- lock the device screen;
- unlock the device screen;
- start intercepting SMS;
- stop intercepting SMS;
- show push notifications;
- re-display the phishing window over the specified application;
- launch a keylogger;
- stop the keylogger;
- remove the applications specified in the command;
- remove yourself as well as the dropper from the device.
Επιπλέον, the Trojan intercepts and sends to the server the content of all Push notifications received by the device. In order to demonstrate a phishing window, the malware uses what has already become a classic for mobile bankers: the contents of such a window are downloaded from a remote server and placed in a WebView that imitates the appearance of the target program to deceive the victim.
Να θυμίσω ότι το είπαμε και αυτό Οι ερευνητές προειδοποίησαν για νέο ransomware DarkRadiation.




