SteamHide כיידז מאַלוואַרע אין פּאַרע פּראָפיל בילדער
G Data analysts have discovered an unusual SteamHide method that hides malware in the metadata of images on Steam profiles.
For the first time, strange pictures on Steam were discovered by cybersecurity researcher Miltinhoc, who talked about his find on טוויטער at the end of May 2021.Researchers at G Data say that at first glance, such pictures are harmless. Standard EXIF tools do not detect anything suspicious in them, except that they warn that the data length in the ICC profile is incorrect.
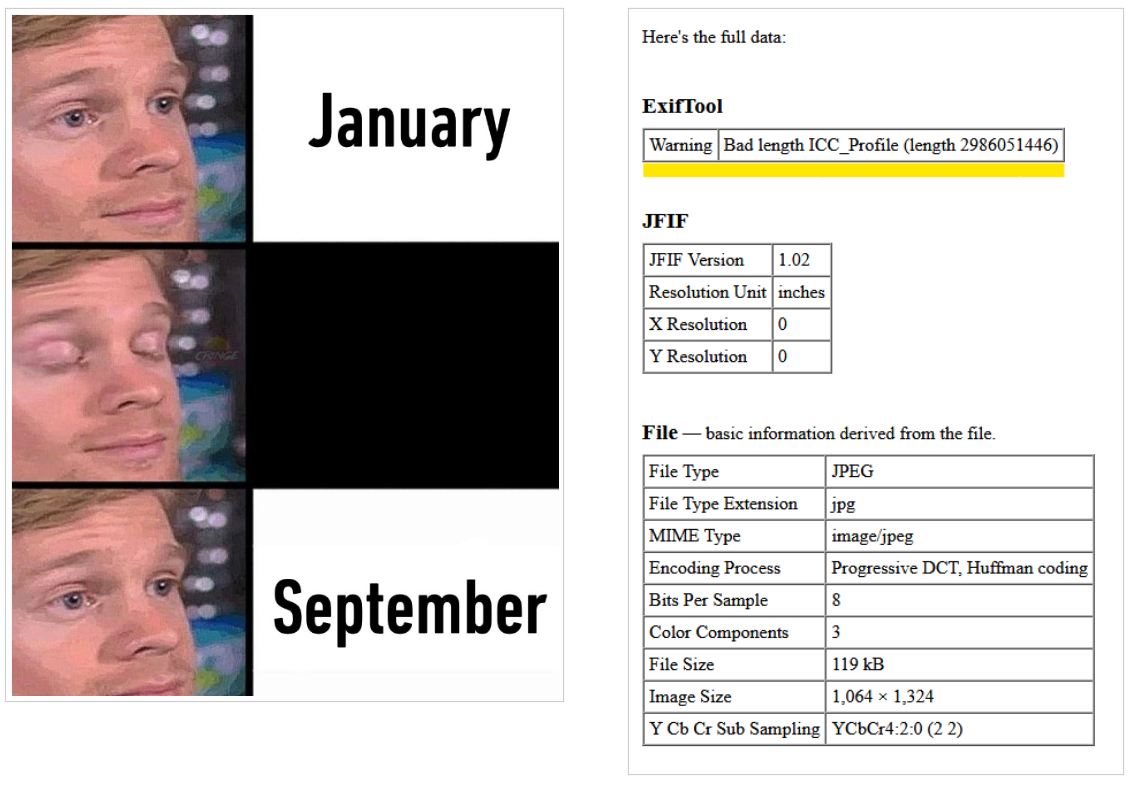
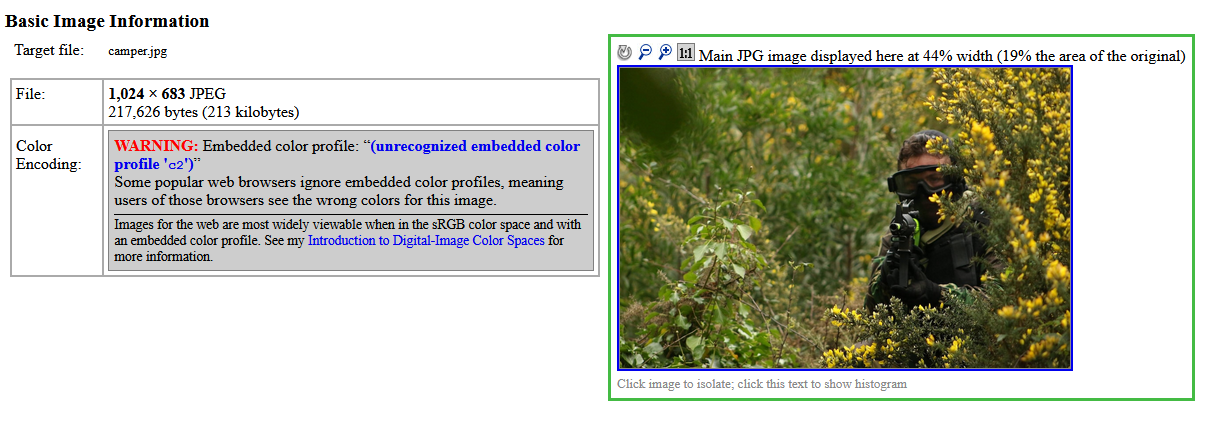
אָבער, in reality, instead of an ICC profile (which is usually used to display colours on external devices, such as printers), such images contain encrypted malware (inside the PropertyTagICCProfile value).
Overall, hiding malware in image metadata is not a new phenomenon at all, the researchers admit. אָבער, using a large gaming platform such as Steam to host malicious images complicates matters significantly. Attackers are able to replace malware at any time, just as easily as changing the profile picture file.
אין די זעלבע צייט, Steam simply serves as a tool for hackers and is used to host malware. All of the bulk of the work involved in downloading, unpacking, and executing such a payload is done by an external component that accesses the Steam profile image. This payload can also be distributed in the usual way, in emails or through hacked sites.
The experts emphasize that the images from Steam profiles themselves are neither “infectious” nor executable. They are only a means to carry the actual malware, which requires a second malware to extract.
The second malware was found by researchers at VirusTotal and it is a downloader. It has a hard-coded password “{PjlD \bzxS#;8@\x.3JT&<4^MsTqE0″ and uses TripleDES to decrypt payloads from pictures.
On the victim’s system, the SteamHide malware first requests Win32_DiskDrive for VMWare and VBox and exits if they exist. The malware then checks to see if it has administrator rights and tries to elevate privileges using cmstp.exe.
On first launch, it copies itself to the LOCALAPPDATA folder using the name and extension specified in the configuration. SteamHide is pinned to the system by creating the following key in the registry: \Software\Microsoft\Windows\CurrentVersion\Run\BroMal
The IP address of the managing server SteamHides is stored on Pastebin, and can be updated through a specific Steam profile. Like the loader, it extracts the executable from PropertyTagICCProfile. דערצו, the configuration allows him to change the ID of the image properties and the search string, דאס איז, in the future, other image parameters can be used to hide malware on Steam.
פֿאַר בייַשפּיל, the malware checks if Teams is installed by checking for the presence of SquirrelTemp\SquirrelSetup.log, but after that no one happens to this information. Perhaps this is necessary to check installed applications on the infected system so that they can be attacked later.
The specialists also discovered the ChangeHash() stub, and it looks like the malware developer is planning to add polymorphism to future versions. The malware can also send requests to Twitter, which in the future can be used to receive commands via Twitter, or the malware can act as a Twitter bot.
Let me remind you that Researchers discovered Siloscape malware targeting Windows Server containers and Kubernetes clusters.




