Evil Corp sử dụng phần mềm độc hại Macaw mới cho các cuộc tấn công ransomware
The hack group Evil Corp (aka Indrik Spider and Dridex) began using the new Macaw Locker (or simply Macaw) malware for attacks. Experts attribute this to US sanctions, which do not allow victims to pay ransoms to attackers.
Researchers remind that Evil Corp has existed since at least 2007, but at first hackers more often acted as partners of other groups. Only later did Evil Corp begin to focus on its own attacks, creating the well-known banking Trojan Dridex.
Over time, as ransomware attacks began to generate more revenue, Evil Corp launched its own ransomware BitPaymer, delivering it to victims’ machines via Dridex. The latter gradually evolved from a common banker into a complex and multifunctional tool.
Eventually, the group’s activities attracted the attention of the American authorities. In 2019, the US authorities brought charges against two Russians who, according to law enforcement officials, were behind the development of Dridex malware and other malicious operations. Cũng, the US authorities imposed sanctions on 24 organizations and individuals associated with Evil Corp and the mentioned suspects.
As a result, negotiating companies, which usually negotiate ransom payments and decryption of data with extortionists, refused to “work” with Evil Corp to avoid fines and lawsuits from the US Treasury Department.
In response, Evil Corp began renaming its ransomware and masking operations to avoid sanctions. Ví dụ, the group’s arsenal includes such ransomware as WastedLocker, Hades and Phoenix, and PayloadBIN. Evil Corp is also believed to be behind the recently rebranded ransomware DoppelPaymer that was named Grief (or Pay or Grief).
Recent attacks on Olympus Và Sinclair Broadcast Group have been linked to the same Macaw Locker ransomware, which appears to be the new brainchild of Evil Corp., Bleeping Computer now reports.
Other unnamed sources in the cybersecurity industry shared with the publication the personal pages of the victims of Macaw, where attackers are demanding ransoms in the amount of 450 bitcoins ($28 million) for one attack and $40 million for another. It is not yet clear which buyout applies to which company.
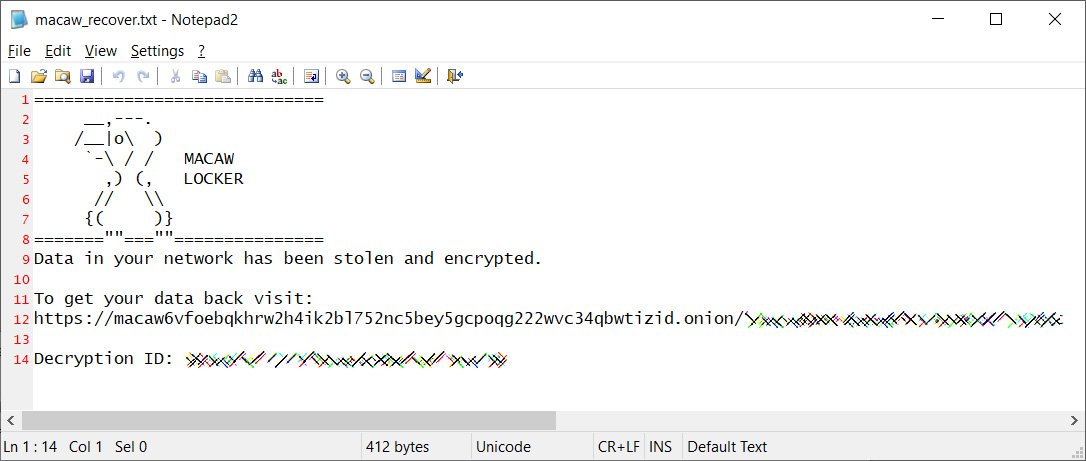
The group’s darknet site contains only a brief description of what happened to the victim, a tool to decrypt three files for free, and a link to a chat room to talk to the attackers.
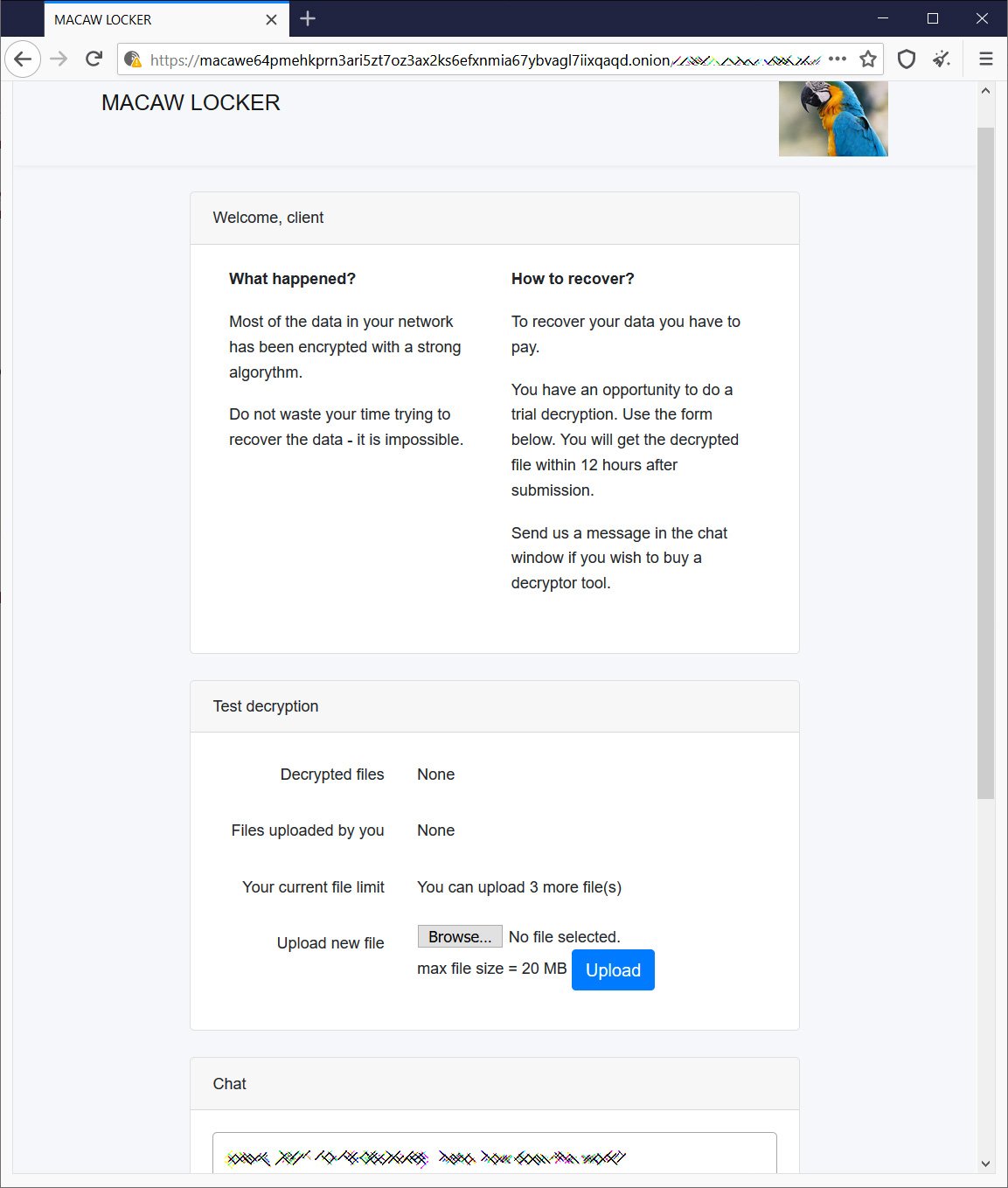
Hãy để tôi nhắc bạn rằng chúng tôi cũng đã viết rằng Grief ransomware threatens to destroy victims’ data if they turn to negotiators.




