TrickBot got a new module for monitoring victims
ตาม จุดตรวจ, TrickBot remains one of the most active threats in the world, even acquiring new module for tracking victims. It also seems that TrickBot takes precedence in the ranking of the most active malware for the second month in a row.
After the Emotet botnet was destroyed by law enforcement agencies, TrickBot activity continues to grow.
ดังนั้น, in June 2021, TrickBot attacked about 7% of companies around the world, and researchers remind that ransomware groups (ตัวอย่างเช่น, Ryuk and REvil) use different malware at the initial stages of infection, but the main one is still TrickBot.
Let me remind you that TrickBot is one of the largest and most successful malwares today. Malware was first spotted back in 2015, shortly after a series of high-profile arrests that significantly changed the composition of the Dyre hack group.
นานนับปี, malware has evolved from a classic banking Trojan designed to steal funds from bank accounts to a multifunctional dropper that spreads other threats (from miners to ransomware and info-stealers). ตัวอย่างเช่น, TrickBot is used by such well-known ransomware as Ryuk, Conti and REvil.
In the fall of 2020, a large-scale operation was carried out aimed at eliminating TrickBot. It was attended by law enforcement agencies, specialists from the Microsoft Defender team, the non-profit organization FS-ISAC, as well as ESET, Lumen, NTT and Symantec. At that time, many experts wrote that although Microsoft was could disable the TrickBot infrastructure, most likely the botnet will “survive” and eventually its operators will put into operation new control servers and continue their activity. น่าเสียดาย, this is what happened.
Bitdefender experts write that the malware developers have recently updated the VNC module (vncDLL), which is used after attacks on particularly important targets. The updated module is called tvncDLL and allows attackers to spy on their victim, collecting information that will allow the attack to be transferred to the most important systems on the victim’s network.
The tvncDLL module was spotted back in mid-May this year, but it is still under development, and the hack group has an “update schedule that regularly adds new features and fixes bugs.”
Analysis of the module shows that it uses a custom communication protocol and communicates with the control server through one of nine proxy IP addresses, which provides access to victims behind firewalls.
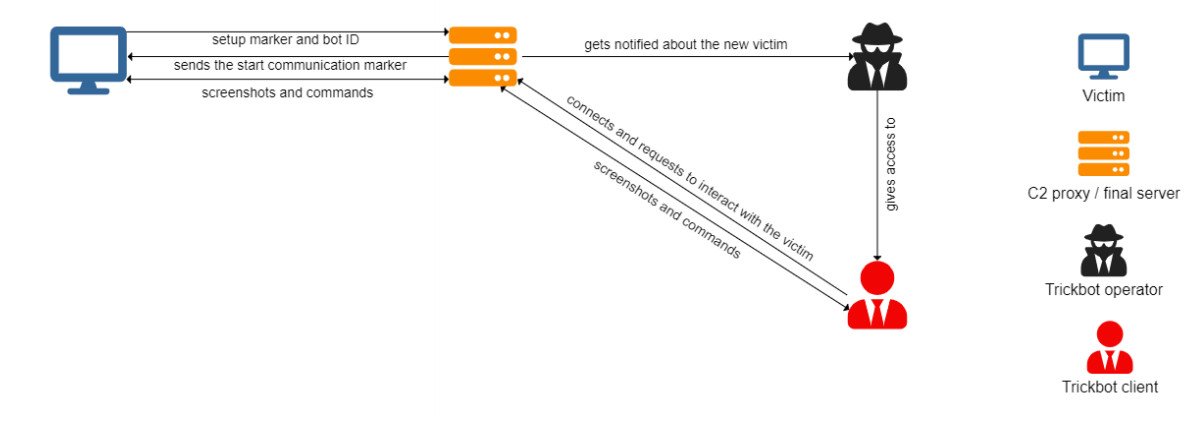
The VNC module can stop TrickBot from running and even unload malware from memory. When the malware operator initiates communication, the module creates a virtual desktop with a custom interface.
Using the command line, malware operators can download fresh payloads from their C&เซิร์ฟเวอร์ซี, open documents and mail, and steal other data from a compromised system.
Another option, called Native Browser, generally launches the browser using OLE automation in Internet Explorer. This feature is under development and is designed to steal passwords from Google Chrome, มอซิลลา ไฟร์ฟอกซ์, Opera and Internet Explorer.
ฉันขอเตือนคุณว่าฉันเขียนแบบนั้นด้วย Researchers linked TrickBot developers with Diavol ransomware.




