DoppelPaymer ransomware renamed to Grief
Bleeping Computer writes that the DoppelPaymer ransomware operators have “rebranded” their product and now the malware is renamed as Grief (or Pay or Grief).
DoppelPaymer’s activity almost came to naught after the scandalous attack by the DarkSide ransomware on the Colonial Pipeline company, after which it was forbidden to advertise and discuss ransomware on the largest hack forums, and many groups preferred to pull back for a while.
Emsisoft expert Fabian Vosar was the first to draw Bleeping Computer’s attention to the fact that Grief and DoppelPaymer is same threat. Although the attackers tried to make Grief different from DoppelPaymer, the similarity was still obvious to experts. In particular, the hackers used the same format for encrypted files and the same malware distribution channel – the Dridex botnet.
The first news of Grief came in early June (although a sample was found compiled on May 17), and then researchers assumed it was a new threat.
But now, Zscaler has examined an early sample of Grief and noticed that the ransom note points to the DoppelPaymer site, as Grief’s own site was apparently not yet ready at the time.
At the moment, on the Grief website, you can already find references to two dozen victims, while the DoppelPaymer website has not been updated since May 2021.
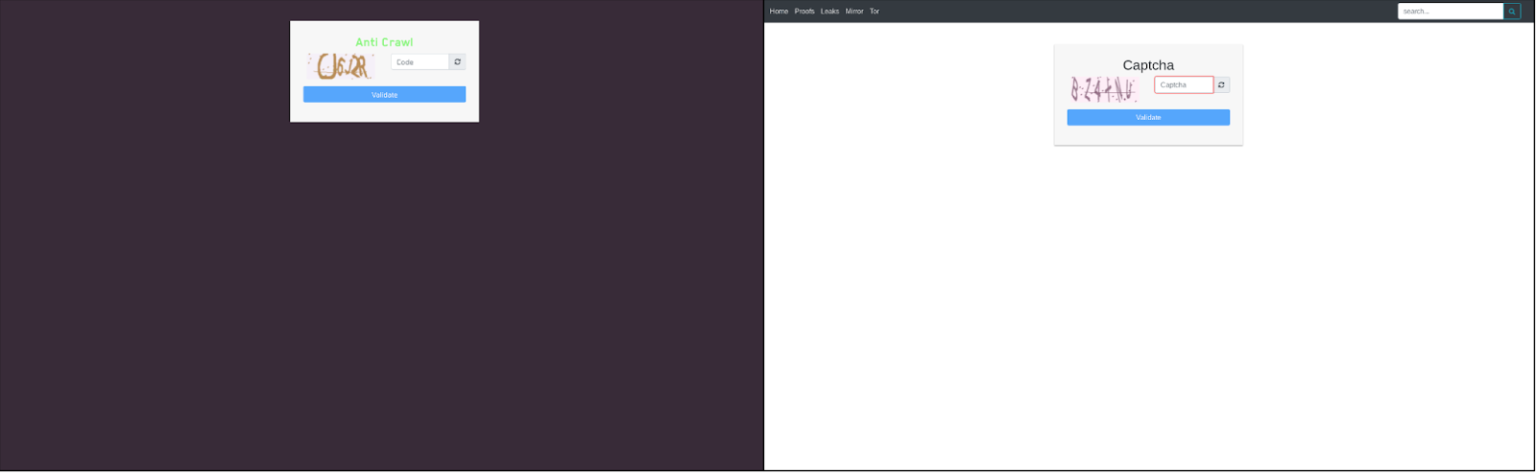
Even the captcha on the ransomware sites are the same.
اس کے علاوہ, it is noted that both malware is based on a very similar code, which, مثال کے طور پر, implements “identical encryption algorithms (2048-bit RSA and 256-bit AES) and import hashing.” بھی, Grief and DoppelPaymer both use the GDPR to put pressure on victims and remind them that in case of a data breach, they will have to face legal consequences.
And adding that hackers have been keeping a low profile lately to avoid the unnecessary attention that REvil ransomware received after hacking clients. Kaseya, and DarkSide after the attack on the Colonial Pipeline.
Let me remind you that I also wrote that Researchers linked TrickBot developers with Diavol ransomware.




