Strange malware prevents victims from visiting pirate sites
SophosLabs experts write that they have discovered a strange malware that blocks pirate sites by modifying the HOSTS file on the infected machine.
The malicious campaign was active from October 2020 to January 2021, but as a result, the attackers’ site went offline.“One of the strangest cases I’ve come across lately: One of my lab colleagues recently told me about a malicious campaign whose primary goal does not seem to align with all of the most common malware motives. Instead of trying to steal passwords or extort a ransom from the owner of the computer, this malware blocks the victim’s access to a large number of pirated software sites by modifying the HOSTS file on the infected system”, — Andrew Brandt, SophosLabs Principal Investigator said.
According to Brandt, the malware actively used tools that it fought against, as Discord and torrent trackers with pirated software to spread. On Discord, the malware was distributed as separate executables that pretended to be pirated software, as shown in the illustration below.
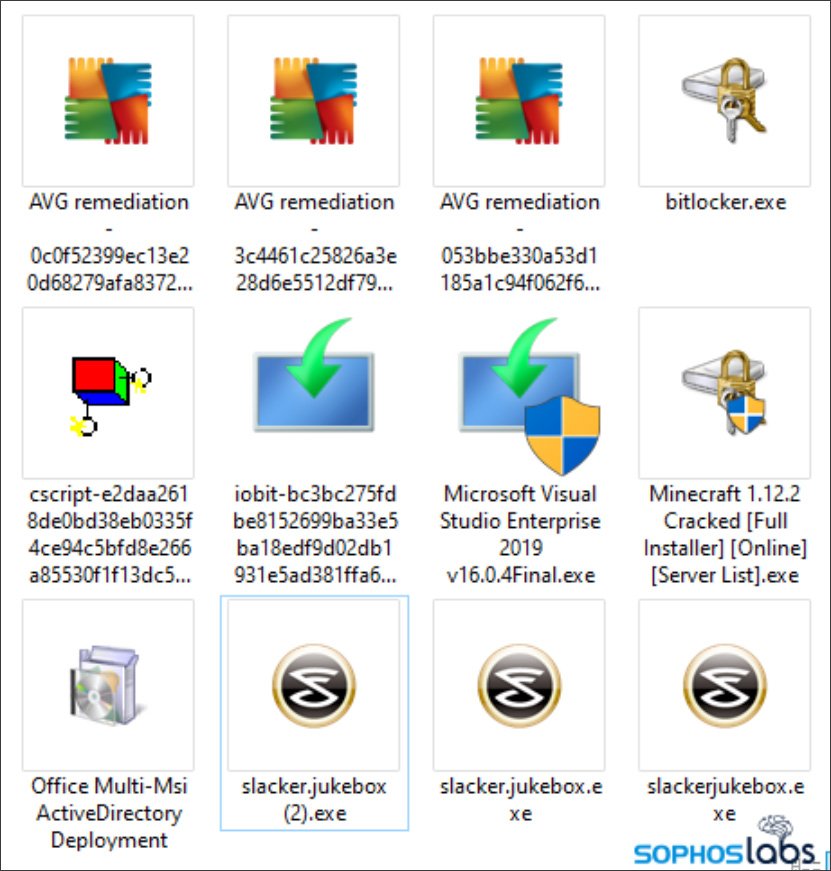
At first glance, on torrent trackers like The Pirate Bay, malware was distributed under the mask of common distributions, which also had readme, NFO files and shortcuts leading back to thepiratebay.org.
อย่างไรก็ตาม, in reality, many files in such torrents did not make any sense and were added as a “stub” to make the malware look like a typical torrent file with pirated software or a movie.
“After having a closer look at the files associated with the installer, it becomes clear that they have no practical use and are intended to give the archive the usual look, which usually has content distributed through Bittorrent, they may also increase the hash values by adding random data”, — explains the expert.
If the user downloaded and ran such malware, it would modify the HOSTS file on the victim’s system, adding numerous entries for pirate sites (mostly related to The Pirate Bay) pointing to 127.0.0.1.

The malware also connected to a remote site under the control of hackers and passed to its operators the name of the fake pirate soft, due to which the user became infected. Since web servers usually register IP addresses, attackers learned both the IP address of the unlucky pirate and the name of the software or movie that the pirate was trying to download.
It is not known why this information is used by attackers, but the researcher warns that hackers can share it with ISPs, copyright holders, or even law enforcement agencies. อีกด้วย, malware creators can use this data in further attacks, ตัวอย่างเช่น, extorting money from users for silence.
ฉันขอเตือนคุณว่าฉันเขียนแบบนั้นด้วย ผู้เชี่ยวชาญได้ค้นพบมัลแวร์ที่ไม่รู้จักซึ่งขโมยมา 1.2 TB ของข้อมูลที่เป็นความลับ.




