New XLoader malware steals credentials from macOS and Windows
Check Point experts talked about a new cross-platform malware XLoader, a “subscription” to which costs only $49 on the darknet. XLoader provides the opportunity to collect credentials, can act as a keylogger and runs malicious files.
XLoader originated from the well-known Formbook malware family, which mainly attacked Windows users, but disappeared from the market in 2018. In 2020, Formbook was renamed XLoader.
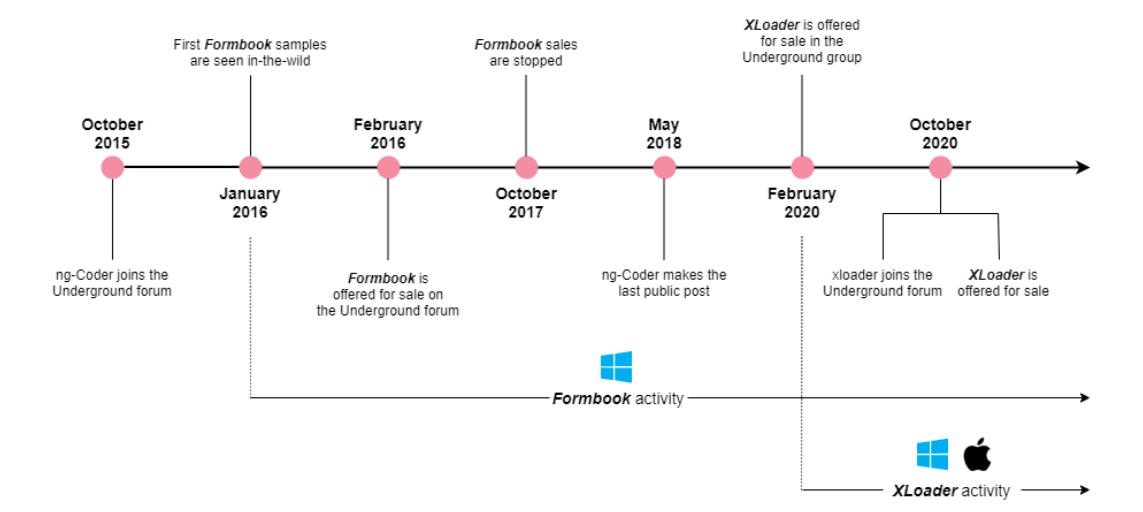
XLoader was first spotted last February and has gained popularity by promoting it as a cross-platform (Windows and macOS) botnet with no dependencies. The connection between the two malwares was established after it was discovered that the new malware uses the same executable file as the Formbook earlier. Then the malware vendor explained that the Formbook developer had really contributed a lot to the creation of XLoader. Because of this, malware has very similar functionality (stealing credentials, taking screenshots, keylogging, and executing malicious files).
Looking at XLoader activity over the past six months, Check Point analysts found that it now targets not only Windows users, but macOS users as well. You can “rent” the version for macOS for $49 a month, having access to a server provided by the seller. By maintaining a centralized management infrastructure, malware authors can control how their clients use XLoader.
The Windows version is more expensive, as for it the the seller asks for $59 per month, vagy $129 for three months.
As mentioned above, researchers tracked Xloader activity from December 1, 2020 to June 1, 2021, and during this time they recorded requests to buy XLoader from hackers from 69 countries. Ráadásul, more than half (53%) of malware victims live in the United States.
Let me remind you that I also wrote that Researchers discovered Siloscape malware targeting Windows Server containers and Kubernetes clusters.




